Dogecoin’s usecases have seemingly evolved over time.
The meme coin was initially created as a joke in 2014, turned into one of the hottest cryptocurrencies in 2015, became Elon Musk’s favorite in 2018, and was part of a TikTok challenge in 2020.
But things have taken a darker turn for the currency; hackers are now utilizing the token to control crypto mining botnets, security firm Intezer Labs said in a report this week.
Such DOGE, much hack
Intezer Labs, a New York-based malware analysis and detection firm, found out hackers using the infamous “Doki” backdoor have been using Dogecoin wallets to mask their online presence.
The firm said it had been analyzing Doki, a trojan virus, since January 2020 but recently discovered its use in installing and maintaining crypto-mining malware later.
A hacker — who goes by Ngrok — had uncovered a method to use Dogecoin wallets for infiltrating web servers, the firm noted.
The usage is a first such case for the meme coin, which is otherwise known for funnier purposes.
Intezer Labs found out Doki was using a previously undocumented method to contact its operator by abusing the Dogecoin blockchain in a unique way in order to dynamically generate its control and command (C&C) domain addresses.
Using Dogecoin transactions allowed the attackers to alter these C&C addresses on any affected computers, or servers, that ran Ngrok’s Monero mining bots.
Doing so allowed the hacker/s to mask their online location, thus preventing detection by legal and cybercriminal authorities.
Intezer Labs explained in its report:
“While some malware strains connect to raw IP addresses or hardcoded URLs included in their source code, Doki used a dynamic algorithm to determine the control and command (C&C) address using the Dogecoin API.”
The firm added these steps meant security firms needed to access the hacker’s Dogecoin wallet to take down Doki, which was “impossible” without knowing the wallet’s private keys.
Using DOGE to control servers
Using Doki allowed Ngrok to control their newly-deployed Alpine Linux servers for running their crypto-mining operations. They used the Doki service to determine and change the URL of the control and command (C&C) server it needed to connect for new instructions.
Intezer researchers reverse-engineered the process, detailing the initial steps as shown in the image below:
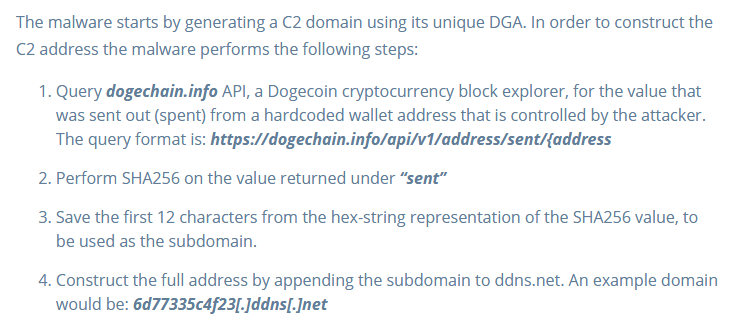
When the above was fully executed, the Ngrok gang could change Doki’s command servers by making a single transaction from within a Dogecoin wallet they controlled.
However, this was just part of a larger attack. Once the Ngrok gang gained access to command servers, they deployed another botnet to mine Monero.
Dogecoin and Doki only served as access bridge, as ZDNet researcher Catalin Cimpanu tweeted:
Intezer said Doki has been active since this January, but remained undetected on all 60 “VirusTotal” scanning software used on Linux servers.
As of today, the attack is still active as of today. Malware operators and “crypto-mining gangs” have been actively using the method, said Intezer.
But it’s not a big worry.
The firm says preventing exposure to the virus is easy; one just needs to ensure that any critical application process interfaces (APIs) are fully offline and not connected to any application which interacts with the internet.
Source: cryptoslate.com

Comments
Post a Comment